Cyber attacks rarely respect boundaries between infrastructure, applications, and cloud services. Attackers exploit the weakest link — whether that’s an exposed server, a misconfigured cloud service, or a flaw in application logic.
Metis Security delivers professional penetration testing services that combine infrastructure penetration testing and web application penetration testing into a single, cohesive assessment or as separately as you desire. Our testing is designed to reflect real-world attack techniques, providing clarity on genuine risk rather than overwhelming you with low-value findings.
We assess on-premise, cloud, and hybrid environments, including Azure infrastructure, alongside public-facing and internal web applications and APIs. By testing across layers, we identify how vulnerabilities can be chained together to achieve meaningful impact.
Every engagement is tailored. We work with you to understand your business objectives, compliance drivers, and risk appetite, ensuring testing activity and remediation guidance align with what matters most to your organisation.
Our penetration testing services focus on depth, accuracy, and actionable outcomes — helping you make informed decisions and measurably improve your security posture.
The process for a Infrastructure Security Assessment typically involves a number of steps. The first of which is a free of charge consultation, followed by a number of of charged engagement activities. Once the report has been assessed, we can help you with any remediation work you may require and potentially engage in further follow up activities.
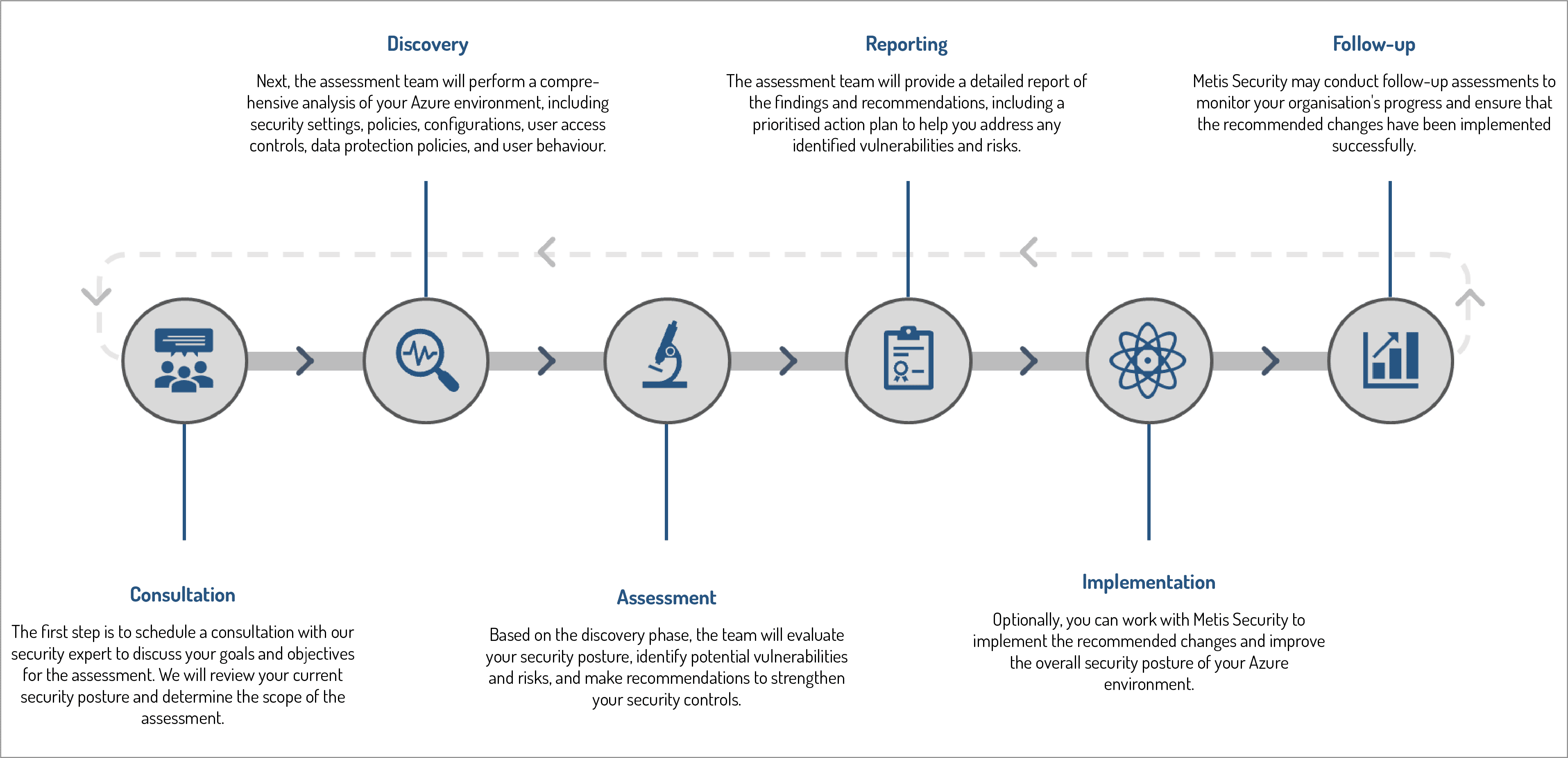
Elevate your infrastructure security with Metis Security. Experience the benefits of proactively identifying security weaknesses, seamless integration with Azure Security Assessment, personalised recommendations, and ongoing support.
Penetration testing requirements vary depending on scope, complexity, and technology. The examples below are indicative only — all engagements are bespoke and carefully scoped.