Vulnerability scanning and penetration testing are often talked about as if they are interchangeable — but they serve very different purposes. Many organisations rely heavily on automated scanning to demonstrate security activity, yet still struggle to answer a more important question: what could an attacker actually do? This article explains the difference between vulnerability scanning and penetration testing, shows how they fit together, and why the distinction matters. We’ll compare both approaches, illustrate how real-world risk emerges through attack paths rather than isolated findings, and address common questions about cost, value, and assurance. Finally, we’ll explain why Metis Security prioritises penetration testing as the most reliable way to understand and reduce meaningful security risk.
Vulnerability scanning is useful for:
Penetration testing is essential when:
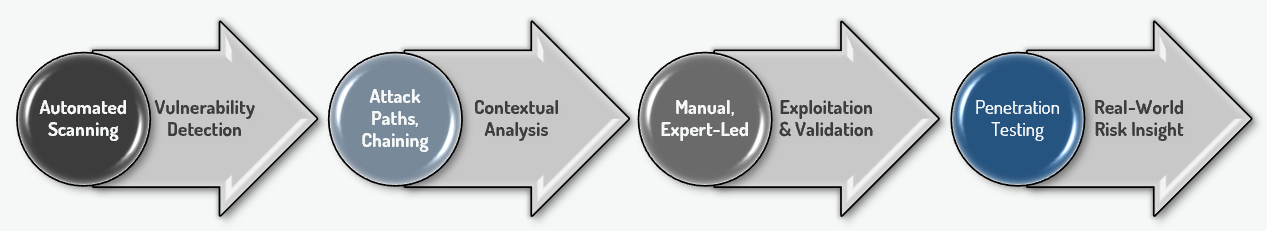
Automated scanning identifies what might be wrong.
Penetration testing shows what actually matters.
Our approach prioritises real-world impact, manual verification, and clear remediation guidance — so you can make confident security decisions.
Trusted Microsoft Cloud Security Advisor with 27 years experience | Empowering Businesses to Embrace Cloud Innovation with Confidence